Hi, I'm back from vacation. And now I'm catching up on all the things that have happened during that time. So, here's a short writeup regarding publicly-known IDA bug and how it will (not) affect reversers.
It was supposed to be a long post showing how to use PatchDiff to locate patched code and then backport it. But, as you'll see later, that's not necessary at all. Maybe another time..
Initial research by Palo Alto
When checking my RSS feed, I stumbled upon the article by Palo Alto researchers called "The Dukes R&D Finds a New Anti-Analysis Technique". It stated:
Using the exported functions by ordinal meant the exported function name was unnecessary, which allowed the developer of this DLL to leave the names for the exported functions blank ... The less obvious reason is that it takes advantage of a bug in the popular IDA disassembler that was recently fixed in the latest version of IDA.
Bug in IDA?! How nice, I want to test this!
Testing the bug
Palo Alto report contained most of the information to reproduce the issue. But IDA 6.95 changelog was even more detailed about what was fixed:
BUGFIX: PE: IDA would not detect DLL exports with empty names
BUGFIX: PE: IDA would show no exports if the export directory's DLL name was an empty string
Armed with the detailed description, I used MASM32 package and their Examples to build a DLL file.
Empty DLL name
First, I took hex editor and changed DLL name in export directory.
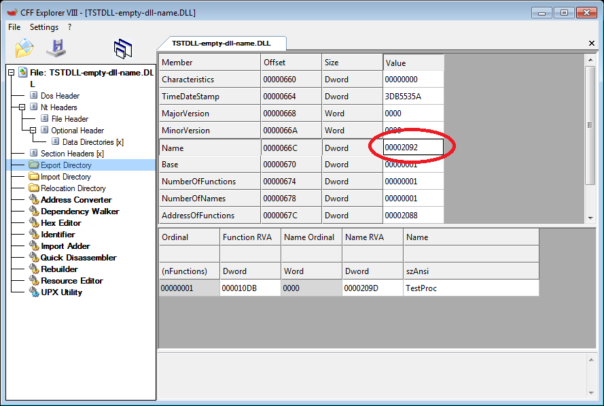
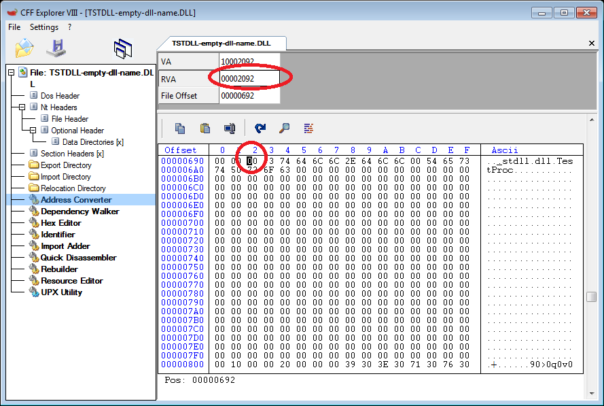
Now the exported DLL name is 0-length string. Let's see what IDA does..
I started with IDA 6.95 Demo you can download from official site. No surprises here, the bug is fixed:
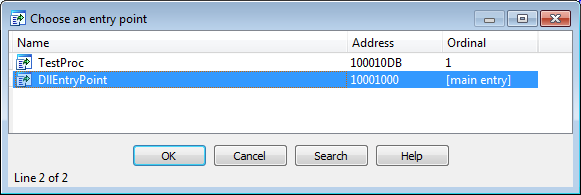
Then I took legit copy of IDA 6.90. As already demonstrated by Palo Alto, it's buggy:
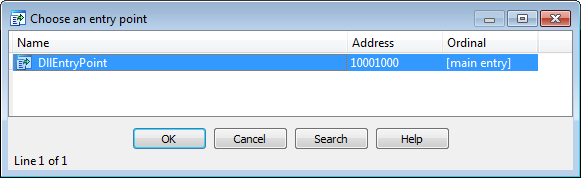
Naturally, I wanted to see how old this bug is. So, I took a copy of IDA 6.80. Surprise, surprise, it's not buggy!
So, it looks like this bug was introduced in IDA 6.90.
Empty export name
For completeness sake, I repeated the experiment with empty exported API name.
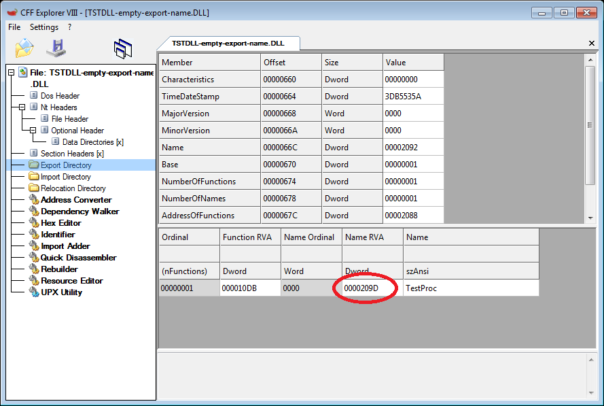
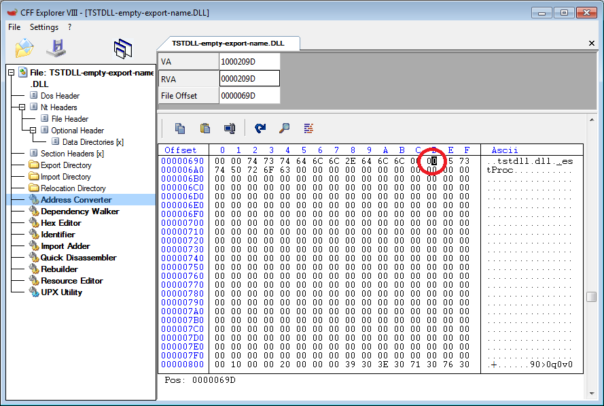
The results were identical, the bug is only present in IDA 6.90.
How it affects you?
If you're using IDA Free, latest version is 6.95. You're good.
If you're using legit IDA, you have received the updated version 6.95. You're good.
If you're using the latest publicly leaked version of IDA (6.80), it didn't have the bug. So, you're good, too.
To sum it up - it's a fun bit of information but no one is really affected. Good news, I guess. smile
Example DLL files if you want to verify your tools: https://www.mediafire.com/?c9t6hm4icd3kk46






