Local Privilege Escalation Bug in Faronics Deep Freeze
While preparing update for Meltdown, I encountered a textbook error in Faronics Deep Freeze Enterprise v8.31. So, here goes..
Running With Unnecessary Privileges
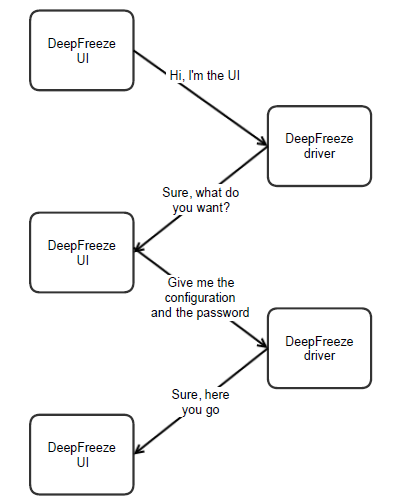
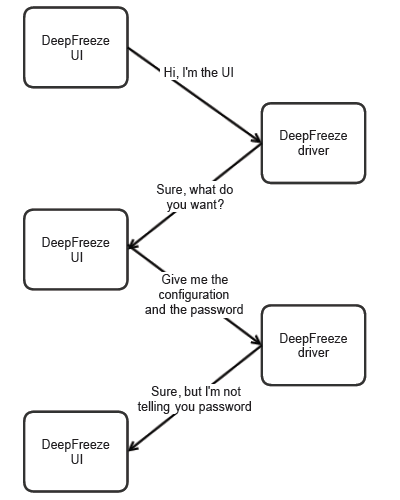
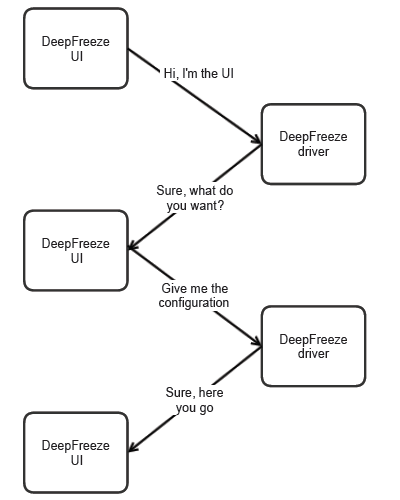
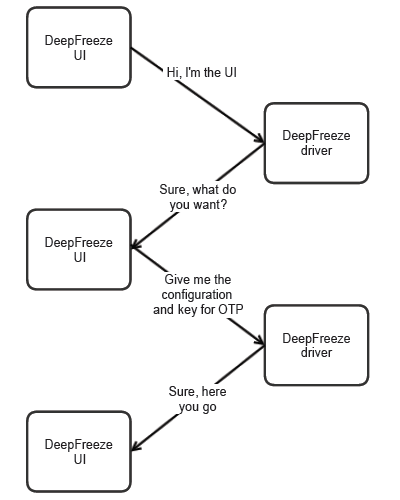
frzstate2k.exe is application responsible for displaying Deep Freeze Workstation Configuration dialog. To do that, it sits in the system tray and communicates with DeepFreeze driver.
For reasons I really can't understand, this simple UI component is executed under SYSTEM account. To make matters worse, it doesn't even drop unnecessary privileges. All these are textbook errors and Microsoft has spent last 10+ years trying to educate programmers and eliminate these kinds of bugs.
Here's the great presentation from Black Hat 2006 about this subject (slides 7-15): Security Engineering in Windows Vista
Abusing Common Dialogs
Microsoft Windows provide APIs for creating nice standard dialogs like "Open File.." and "Save As.." These dialogs are heavily integrated with Windows shell and offer much more than just file selection - within the dialog box you can do almost anything you can do using Windows Explorer. Like executing other applications..
Due to that, these dialogs are often used to break out of Terminal Server environment or to elevate local user privileges. Here is a quite good tutorial covering the basics: Breaking out of applications.
These attacks are also very old. Here's nice presentation from year 2008: Hacking Internet Kiosk’s
Putting it all together
Here's how any user can get SYSTEM privileges in 5 easy steps:
- user is logged on using low-privilege account,eg. belongs to "users" group;
- user gains access to workstations DeepFreeze administration interface (eg. using password generated by Meltdown);
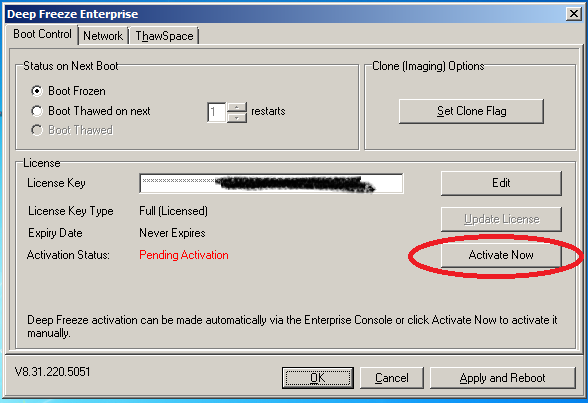
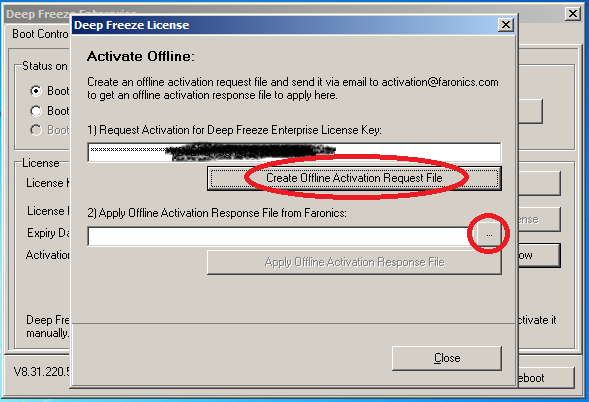
- user presses "Activate Now" -> "Activate Offline" -> "Next" -> and presses either of the 2 buttons that open "Save As" or "Open" dialogs;
- since FrzState2k.exe is running under SYSTEM account, these dialogs give access to anything SYSTEM account has access to.
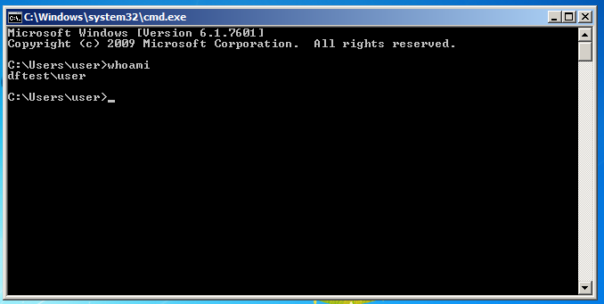
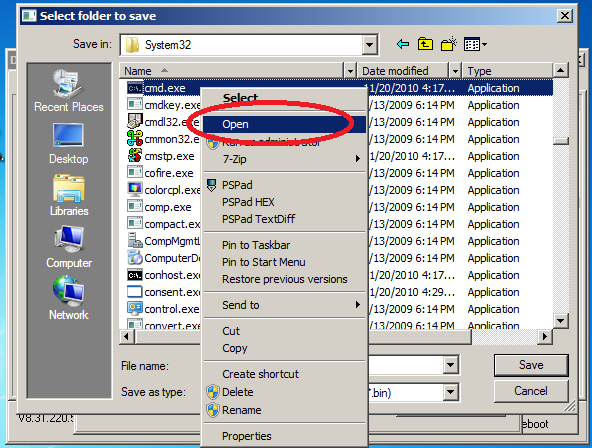
- user navigates to C:\Windows\System32\ , right-clicks cmd.exe, and chooses Open.
- cmd.exe is executed under SYSTEM account.
- game over.
Mitigating factors?
This attack was verified against 30-day evaluation version of Deep Freeze Enterprise. It is possible that after the workstation is activated, the "Activate Now" button is disabled and there's not an easy way to access it. This would (accidentally) limit attacks only to workstations that haven't been activated yet.
Conclusion
It's hard to write anything here without using inappropriate language. Faronics positions itself as a security company, yet their products contain textbook errors like these. Make your own conclusions.