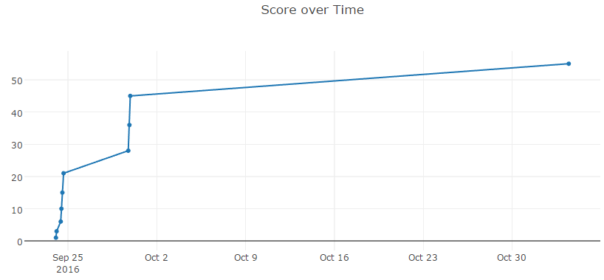
This year's FLARE reverse engineering contest is over. I managed to finish it on time - but I really had to force myself to keep going several times. This graph tells it all:
You can get all the challenges from the official site (password: flare) and there are already a number of writeups all over the web.
I'm not going to reinvent the wheel, so here's just my take on few of the challenges. 🙂
#1 - Challenge1
Time spent: 9 mins. Not much to say, it's designed to be a warmup.. Custom Base64, that's it.
#2 - DudeLocker
Time spent: 1h 20mins. The buzzword for year 2016 is "ransomware". Every self-respecting reversing challenge has to have one. It was fun and kinda easy for me - but in my opinion it was too hard for level 2.
#3 - unknown
Time spent: 7h 45mins. Since challenge starts at 3AM in Europe, one needs to get some sleep..
As for the task - reverser has to figure out the correct filename from PDB entry and then the challenge becomes solvable. No, it doesn't have anything to do with actual reversing, just a random crap obstacle thrown into your way.
#4 - flareon2016challenge
Time spent: 1h 20mins. "Play me a song, have me play along.." Given a DLL, one must figure out the correct order in which to call exported functions to play a song. Original idea, kinda refreshing.. 🙂
#5 - smokestack
Time spent: 1h 45mins. And, of course, every challenge has to have custom Virtual Machine. This one was just the right difficulty and offering several ways to break it. Nice.
#6 - khaki
Time spent: 2h 20mins. Obfuscated python bytecode. Considering that it was my first time directly patching python bytecode, I enjoyed it a lot. In my opinion, one of the most interesting of challenges this year.
Fun fact - opcode for nop in Python is 0x09.
#7 - hashes
Time spent: 5days 2h 22mins. This is where I got really annoyed and stopped playing.
Not only they throw in a Linux challenge into the mix, they use Go programming language and compile binary in a way that requires libgo.so.7 - which is not available on certain Linux distributions (like Debian).
So, one has to figure out which bloody Linux distribution has support for it, install that in a Virtual Machine, then find a way to install Go language, then fight with SELinux - and all that just to be able to debug the binary provided by challenge. That's just frigging stupid. How hard it is to tell the OS requirements before the challenge starts? >:(
Once I got over my enrage and disgust, it was actually pretty easy. My "solution" generated ~60GB of data files - just because I let my hash generation code run while still analyzing the challenge code.. 😉
#8 - CHIMERA
Time spent: 2h 10mins. The actual check was hidden in the DOS stub. There were some nice hints and neat and clean code, I loved everything about this challenge! 🙂
The fact that I got to boot up my Windows XP virtual machine and use debug.exe - that was just an icing on the cake.
#9 - GUI
Time spent: 1h 35mins. Mandatory .NET assembly thrown in the mix. Apparently FLARE team was running out of ideas, so they just used ConfuserEx. Three times.
To solve it, all you need to know is that DNSpy exists. I have no idea why this challenge was put as #9, difficulty wise it was more appropriate as #3..#5.
#10 - flava
Time spent: 35.5 days. Difficulty: 9, fun factor: 0.
This was just frigging stupid. I know, it's a final challenge. But it required so much of a very specialized knowledge, that it's insane.
First you need to get through 3 layers of JavaScript obfuscation. Hard but doable. Then you'll arrive at some serious crypto. Normal person can't know this is bugged Diffie-Hellman key exchange which was used by Angler exploit kit and got broken by Kaspersky Labs. So, if you're not a crypto wizard or you don't focus on exploit kit research, you're screwed.
Once you figure out this crap, you still have to get through 3 layers of Flash. First SWF is easy but second one is obfuscated and solving involves a lot of guesswork. You're supposed to guess that RC4 key is reused and decrypting other binary data with the same key stream will get you the required values to get to 3rd layer. How you're supposed to figure that one out? Well, just "do some random stuff and hope it works™".
The final layer has slightly obfuscated ActionScript code but nothing JPEXS can't handle. It is there just to generate the answer.
Conclusion
If I compare this year's FLARE with LabyREnth, LabyREnth wins hands down. In my opinion LabyREnth's Windows track was much more fun and tasks were much more reverse engineering related. But that's just my opinion..
I wish to express my deepest gratitude to fellow reversers who kept me going when I got really angry and upset: Extreme Coders, fasya and Levis. Your hints were invaluable, thank you so much!