Abusing Microsoft-signed executables
This morning I noticed an article from Cylance named "Graftor Variant Leveraging Signed Microsoft Executable". It's a nice article, so I can really recommend you read it.
TL;DR version: Graftor authors are using DLL hijacking in SrcTool.exe to load their own dbghelp.dll. If antimalware solution trusts executable that's signed by Microsoft (most of them do!) and doesn't check all the DLLs it loads, malicious code will not be detected.
Other vulnerable files
I decided to look for other Microsoft-signed files that could be abused in a similar manner. One quick search for EXE files in folder C:\Program Files (x86)\Windows Kits that also contain string dbghelp.dll and here's the result:
- agestore.exe
- cdb.exe
- dbh.exe
- kd.exe
- mftrace.exe
- ntkd.exe
- ntsd.exe
- srctool.exe
- symchk.exe*
- symstore.exe
- tlist.exe
- tracefmt.exe
- tracepdb.exe
*symchk.exe also requires SymbolCheck.dll.
All these files are statically linked to dbghelp.dll and therefore vulnerable to DLL hijacking. agestore.exe, mftrace.exe, srctool.exe, symstore.exe, tlist.exe, tracefmt.exe and tracepdb.exe are the best targets - if you don't pass any command-line to them, they load dbghelp.dll but don't call any of its APIs and therefore will not crash.
Demo time
Here's a small fake dbghelp.dll you can use for testing: https://www.mediafire.com/?yx677bhxtyc13pu
Place it in the folder with vulnerable EXE lies and run the EXE. If a "DLL Hijacking" messagebox shows up, the EXE is vulnerable. smile Something like this:
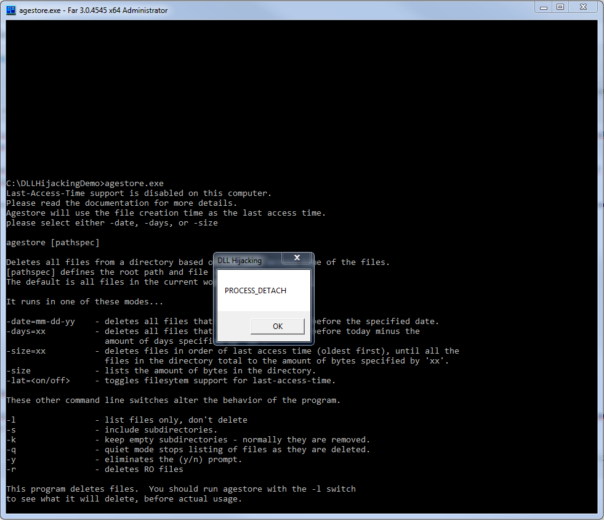
Have fun and keep it safe!
