Sniffing correct serial in .NET crackmes
Introduction
In this tutorial I'll show you a generic way how to break most of the crackmes written in VB.NET. It uses the fact that most crackmes made by beginners will calculate correct serial and do a simple comparison "if enteredSerial = correctSerial then"...
To break such a crackme, you only need to find this comparison and sniff the correct serial. This is a very common approach in x86 world but in .NET world it's not that popular yet.
As for my target, I'm using "RDG Simple Crackme .NET v4 2015"
GetProcAddress in .NET
In x86 world you can use GetProcAddress function to get address of any API function from any DLL. Can we do something similar in managed environment like .NET? It turns out that we can, but it's a little bit harder.
So, for example, to get address of Assembly.Load(byte[]) you need to do:
|
1 2 3 |
MethodBase mb = typeof(Assembly).GetMethod("Load", new Type[] { typeof(byte[]) }); IntPtr handle = mb.MethodHandle.GetFunctionPointer(); Console.WriteLine("Assembly.Load() = {0:X}", handle.ToInt32()); |
This works well with static classes and static methods. How about non-static methods like RijndaelManaged.CreateDecryptor(byte[], byte[])?
That's doable as well, like this:
|
1 2 3 4 |
RijndaelManaged rijndael = new RijndaelManaged(); mb = rijndael.GetType().GetMethod("CreateDecryptor", new Type[] { typeof(byte[]), typeof(byte[]) }); handle = mb.MethodHandle.GetFunctionPointer(); Console.WriteLine("RijndaelManaged.CreateDecryptor() = {0:X}", handle.ToInt32()); |
To make this reference almost complete - here's how to get address of .ctor:
|
1 2 3 |
ConstructorInfo ctor = typeof(MyClass).GetConstructor(Type.EmptyTypes); IntPtr ctorPtr = ctor.MethodHandle.GetFunctionPointer(); Console.WriteLine("MyClass constructor = {0:X}", ctorPtr.ToInt32()); |
There are a few gotchas, however..
- In case your target type is located in assembly that's not NGEN'ed yet, I suggest that you use ngen and install the assembly in cache. That can prevent certain problems later.
- Addresses of functions are obviously different in .NET 2.0 and 4.0. You must compile for correct framework version and target the correct .NET assembly.
- Addresses of functions are different for x86 and x64 framework versions, too. Make sure your assembly is compiled correctly.
Sniffing string compare
Suprisingly, string comparison in VisualBasic.NET and other .NET languages is different. It's caused by Option Compare statement present in Visual Basic language. So, if the crackme is made in VB.NET, you need to examine Operators.CompareString(string,string,bool) function. For crackmes made in other languages, you'll need to examine string.Equals(string) or some other variation of this method.
So, using the code I mentioned above, I learned that address of Operators.CompareString(string,string,bool) on my PC is 599F1D30. Now I need to sniff data passed to this function.
There are several possible approaches. You can try using VisualStudio & Reflector plugin as SpoonStudio tried, you can try using ILSpy and it's debugger plugin, or you can inject DLL into crackme process, as suggested by noth!ng - but I prefer to use OllyDbg.
Load crackme in OllyDbg, make sure that all the anti-anti-debug plugins are working, all the exceptions ignored, put a breakpoint on 599F1D30 and hope for the best.
Nope. Operators.CompareString is called literally thousands of times. So, we need to do something smarter.
For example, we can use conditional logging breakpoints in Olly. Those breakpoints are quite slow, but it's still faster than to write some sort of hooking DLL and inject it into crackme. So, we need to set 2 logging breakpoints - one for each string compared. Here is first one:
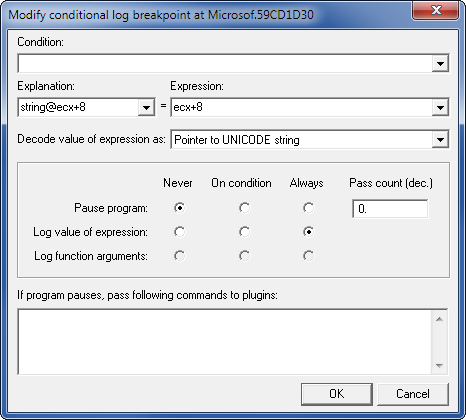
Place second breakpoint at the next instruction (59CD1D31) and log string at edx+8.
Run the crackme, enter some fake but easily recognizable serial and few minutes later we have the answer:
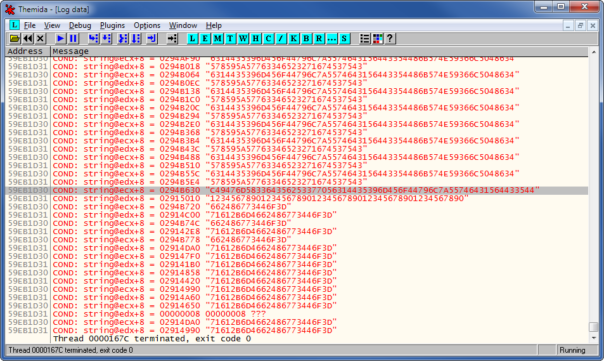
My entered serial was "1234567890123456789012345678901234567890" and it's being compared to "C49476D583364356253377056314435396D456F44796C7A55746431564433544". Hmm, could that be the correct serial for my nickname? wink Yes, it is!
Final notes
This was quite nice crackme and I only showed the simplest way to beat it. When you start looking into it, you'll find some nice anti-debug tricks, some nice anti-patching tricks and pretty nicely obfuscated code.
But that's a matter for another story. Have fun!
Using System.Reflection is not possible if Flag is not == 00020001 (e.g If it's a mixed-mod assembly).
Nice tutorial though, especially the Olly part ! :)
Really, System.Reflection doesn't work? :) I'll check that out later.
To be honest, there are more comfortable solutions to the same problem, for example - Windbg. However, I'm not that comfortable using Windbg and just hate its UI.