Yesterday I read an article on ZDNet called "Researcher finds simple way of backdooring Windows PCs and nobody notices for ten months" and it made my laugh hysterically.
Why? Because it's a bloody nonsense from start to end.
Let's just look at the main claim in the article.
... in cases where a hacker has a foothold on a system --via either malware or by brute-forcing an account with a weak password-- the hacker can give admin permissions to a compromised low-level account, and gain a permanent backdoor with full SYSTEM access on a Windows PC.
What. The. Fuck.
How does this work? Luckily, ZDNet article gives a quick summary:
[Sebastian] Castro, with help from CSL CEO Pedro García, discovered that by tinkering with registry keys that store information about each Windows account, he could modify the RID associated with a specific account and grant it a different RID, for another account group.
Well... To modify a registry entry in the SAM hive on a running system, you must have SYSTEM privileges. But if you already have SYSTEM privileges, you're a God. You can do anything. And to give administrator rights to guest user, you don't need to edit registry, simple net localgroup administrators guest /add will suffice.
This screenshot from the original blog post shows how SAM looks like. To see those data, you must have SYSTEM privileges:
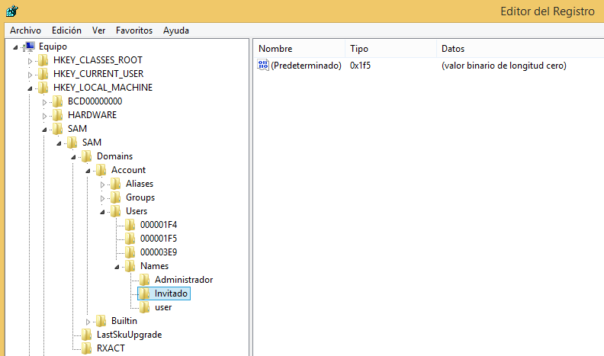
But if you don't have SYSTEM privileges, you won't see SAM contents at all, let alone be able to edit them:
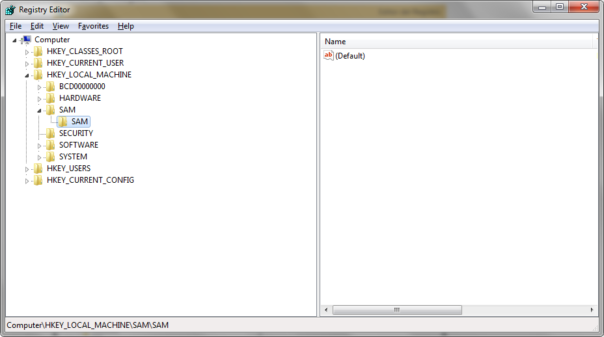
In fact, you can see exactly that in the screenshot graciously provided by Sebastian Castro who "discovered" the "bug":
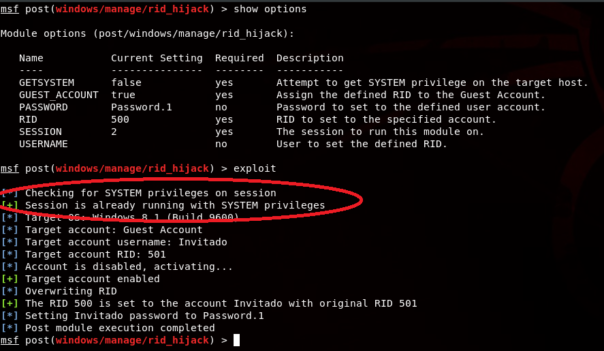
So, in fact it is a Rube Goldberg's way to modify some account settings, nothing else.
Who put you on stage?
Considering that this "discovery" is a total nonsense, it makes me wonder how is it possible that
The researcher has been on a tour this summer, presenting his findings at various cyber-security conferences, such as Sec-T, RomHack, and DerbyCon.
Seriously? Is it possible that these conferences accept any and all submissions and do no vetting process before adding them to the schedule? 😀
Conclusion
Nobody has done anything for 10 months because there's absolutely nothing wrong with Windows (in this case). If you have admin or SYSTEM rights, you can assign group memberships to other users. That's normal and expected.
Dear Mr. Catalin Cimpanu, please stop writing about security. Open a hotdog stand or something, that's much more suitable for your skill level.
Please help us prevent new DeepFreeze activation system (from 8.31 version).
You are the only one who can help!
Hi Dinos,
this blog is not about pirated software. I don't crack activation systems on request. 😉
Hello
Good time
Is there any way to turn movies that were locked up by the password protected video master password without converting it to a movie? And did ANPK do it?
Thank you for helping me
Thanks
This is not piracy, it is fixing software.