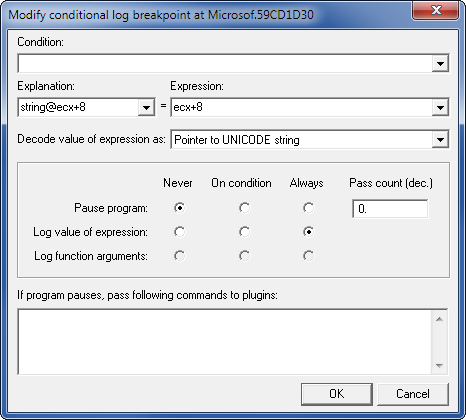
Every other days or two a new guy appears at Tuts4You asking "I want to learn Reverse Engineering, where do I start?".
Hmmm...
There are lots of suggestions, eg. in this Reddit thread. One of the most common recommendation is to with Lena151's tutorials. And there's a good reason for that - these tutorials give a good overview of most common tasks, most common tools and provide "instant gratification". But do they actually teach you Reverse Engineering? I don't think so.
Why Lena151's tutorials are bad
Apparently I'm not the only one who thinks so:
I have been thinking about why this happens. Thinking back to myself, I started learning reverse engineering by reading the Lena151 tutorials. I thought they were awesome until Daeken told me that was an awful approach to learn reverse engineering.
At first I didn’t understand why they were so bad. After all, Lena’s tutorials had taught me how to crack my first software.
And that's exactly the problem. You managed to crack your first software. Instant gratification! But what did you actually learn? Run some common tools, find the "bad boy jump" and patch it? Wow! You must be so l33t!
In reality, these tutorials have produced entire generation of wanna-be-crackers who can only use ready-made tools, but are actually unable to think for themselves. For every problem they need a video tutorial. For every small obstacle they create a new topic asking for help.
And that's only half of the problem.
Video tutorials made by beginners are even worse
Albert Einstein once said:
The more I learn, the more I realize how much I don't know.
Beginners who watched Lena151's series don't realize that. They cracked their first program and they consider themselves to be reversers. And what's even worse, they try to spread their "knowledge" by making an incredible amount of incredibly crappy video "tutorials" to be watched by next generation of wannabes.
I've actually watched a 15 minute movie titled "How to unpack CryptoObfuscator". You know how? You drag-and-drop the file on de4dot. Yes, that simple. Yes, someone made 15 minute movie to teach you that.
So, what's the alternative?
ReverseWithMe blog suggests to learn:
- x86 assembly (electronics and wires in the car analogy)
- How operating systems work and how they manage memory (the engine of the car)
- The compiling process from C-code to assembly (this is equivalent to knowing how a car-fabric is assembling a car)
- The life of a binary (equivalent to everything that happens in the car from the key-switch to the off-switch)
I don't think this is the correct approach either.
It's like learning a foreign language by reading a dictionary. Start with an "a", and once you finish with "z", you'll know all the words. Maybe. But you won't be able to make a proper sentence, let alone speak or understand a native speaker.
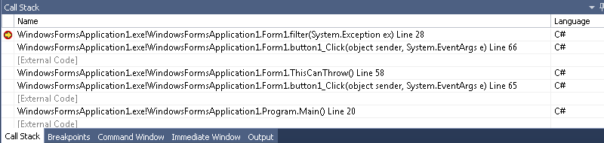
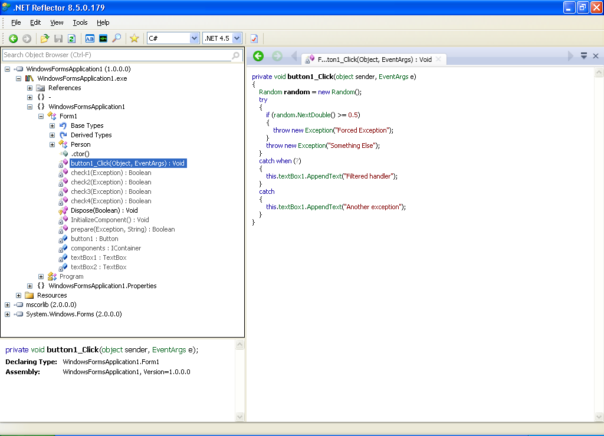
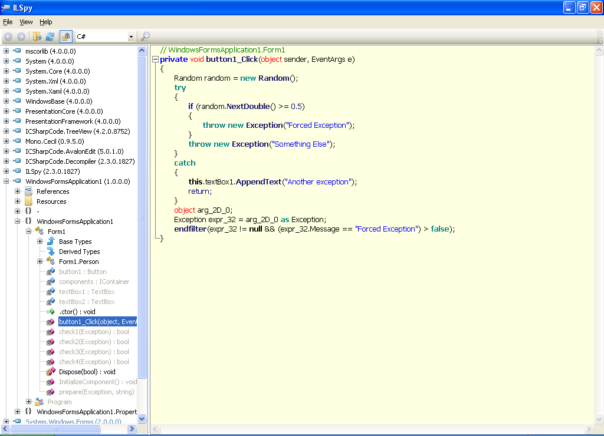
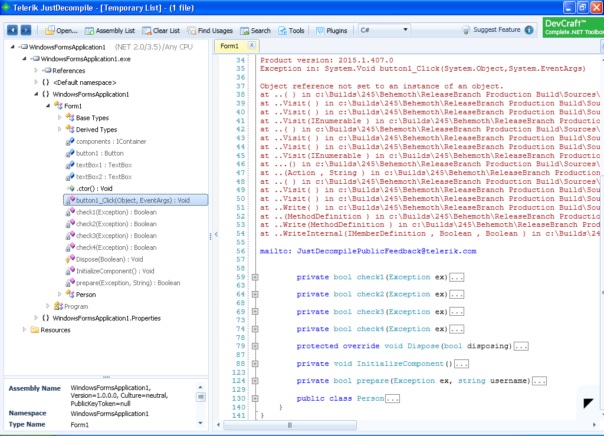
To put it into context: I've been reversing .NET executables for 10 years now. I've written unpackers for pretty much every .NET protection there is. And yet I still don't know IL assembly "by heart". Why? Because I don't need to. What's the mnemonic for "branch-if-equal"? Is it be, beq or bre? Does it pop one or two arguments from stack? I don't know. If I'll ever need that, the answer is one Google search away.
Yes, to be a great reverser, you will need to master most of those items. But you don't need to know all that at the start of your journey.
Gimme a solution, goddamit!
Well, start with Lena151's tutorials. Yes, I said they are not good, but that's the best there is. And if you follow few extra advices, you'll do just fine:
- Learn to think for yourself. That's the most important part. Don't just blindly follow tutorials, try to understand why it works and how it works.
- Learn to search. Most questions have already been answered, you just need to find the answer. Make sure Google is your friend!
- Learn your tools. You don't need to know every single option and feature of them. Most people use ~10% of all Microsoft Excel features. Power Users use around 20%. It's the same with RE tools. If you've mastered 10% of Olly or IDA features, you're good to go.
- And last but not least - have fun! Nothing kills your productivity faster than boredom. If the problem is too hard, let it go, try something else and come back to it later.