JS-boobytrapped ZIP files, or why morons shouldn’t be writing about security
This morning I noticed Softpedia article titled "How to Prevent ZIP Files from Executing Malicious JavaScript Behind Your Back".
Here's the beginning of the story in all it's glory:
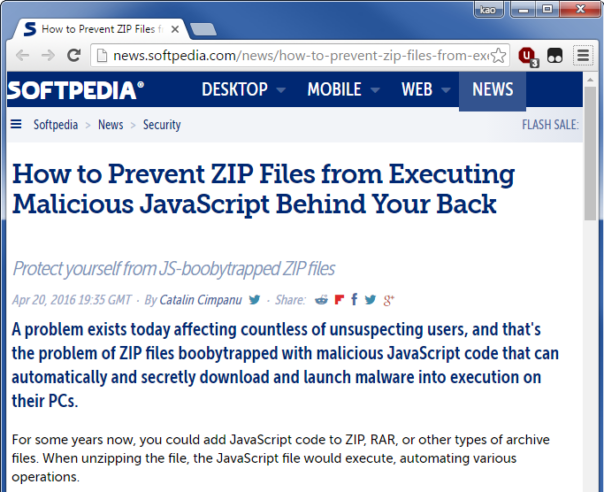
Let me repeat that:
When unzipping the file, the JavaScript file would execute, automating various operations.
Naturally, I was curious about the cause of this issue and why I haven't heard about it before.
Little bit of reading, little bit of Googling and here's the original post from F-Secure: "How-To Disable Windows Script Host". They write:
And such .zip files typically contain a JScript (.js/.jse) file that, if clicked, will be run via Windows Script Host.
Somehow Softpedia authors managed to convert "user clicking on a JS file" into "JS file being launched automatically when unzipped".
Dear Mr. Catalin Cimpanu, please stop writing about security. Open a hotdog stand or something, that's much more suitable for your skill level.
One big LOOOOOOOL :D
When I read the title ... I thought to read about a new vulnerability discovered in Windows zip file handling with lots of technical details I would not have understood. :P
Thank you for this blog post ... it made my day ;)
Best Regards,
Tony
@kao: I really like your conclusion :D
Regards,
basically the whole article is all about "How to prevent the opening of a file with the program assigned to it's extension"...this guy is good at headline whoring
i had a few lols at the end , specially that i'm from the same country as the softpedia's article publisher :)
Glad you liked it. :)
LOL this guy has no shame with his clickbaits:D