tl;dr version - it unpacks stuff. Feel free to leech and reupload. Report bugs here.
Introduction
It all started with a topic on BlackStorm forums where whoknows posted a link to Reverzor - The first cloud based software that decompiles everything!.
Wow, a magic tool that does everything! Sounds too good to be true.. 🙂 Soon enough, li0n posted a link to the trial executable and I started looking into it. I quickly found out that it's written in AutoPlay Media Studio, and that there is no working unpacker for that.
I should fix that - and have some fun in process!
Existing tools and research
First, I found a great blogpost by Xiaopang - I wholeheartedly recommend that you read it.
And then there's a AmsDec.exe by mohsen.
Unfortunately, it only works for some files (supposedly - v8.1, v8.2) and shows weird messages in Persian language. And it's not really a decompiler, it just extracts _proj.dat file from the cdd file. And, of course, it didn't work for Reverzor.
How AutoPlay Media Studio works
So, let's see what we need to do to unpack it all properly. As the authors of AutoPlay Media Studio wrote in changelog:
As we all know, anyone determined enough can break any protection system given enough time and resources, but the use of rolling codes renders generic attacks ineffective. You can now sleep a little easier!
Right... They are using ZIP files protected with randomly generated passwords and obviously have no clue how generic attacks work..
Unpacker needs to analyze EXE file, generate correct password and unzip files. If there's a cdd file, unzip that one too. And since it's that simple, I will use AutoPlay Media Studio as a target for a separate blogpost explaining how to write a static unpacker from scratch. 🙂
Since there are several options how you can distribute files built by AutoPlay Media Studio, here's a quick reference:
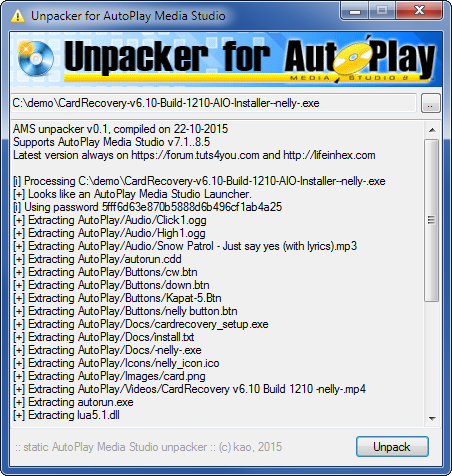
- you have just a single application.exe;
Such files can be generated using "Publish -> Web/Email executable" feature in AutoPlay Media Studio. Example file would be CardRecovery v
6.10 Build 1210 AIO Installer -nelly-.exe
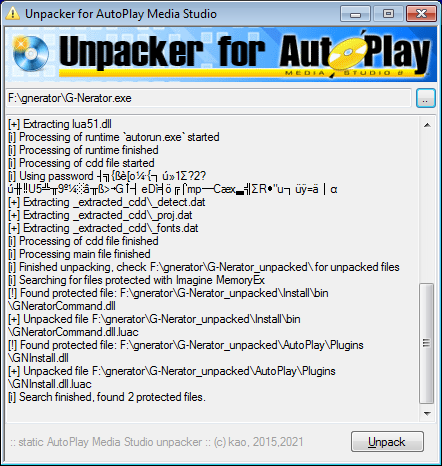
Drop the exe file on unpacker, it will unpack everything automatically. Then check the appropriate folder for extracted data files and _proj.dat for the installation script.
- you have a folder with application.exe and application.cdd in a subfolder AutoPlay;
These files are created using "Publish -> Hard drive folder" in AutoPlay Media Studio. An example file can be, for example, Russian software (malware?) claiming to be a Photoshop installer.
There is not much to unpack, as data files are in plain sight in folder AutoPlay and subfolders. Drop the exe file on unpacker, it will find cdd file automatically and unpack everything, including _proj.dat.
- you have application.exe and application.cdd files in the same folder;
This happens when "Rename resource files" feature is enabled in AutoPlay Media Studio. It's one of those features that add fake security to the product:
This option is designed to obscure the filenames of your resource files during publishing.
This is a case of Users Sniffer. Similar to previous case, there's not much to unpack. Drop the exe file on unpacker, it will find cdd file automatically and unpack everything, including _proj.dat.
Advanced use cases
But sometimes things are not that easy. So, here are few possible scenarios how to deal with modified AutoPlay Studio:
- application.exe is packed and there is application.cdd file present.
This is a case of official AMS studio challenge that Xiaopang mentioned on the blog. Good news - you don't need to be an unpacking wizard and properly unpack PCGuard to break their protection. It's enough to run the EXE in VMWare, dump process memory and drop dumped exe on my tool. As long as PE header and section table is correct, it should be fine.
Step-by-step:
1) Run and dump:
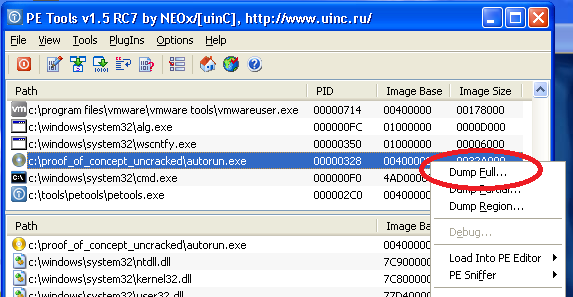
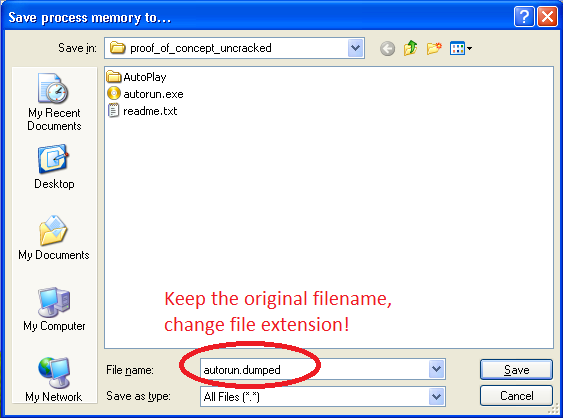
2) When saving dump, keep the original filename. Otherwise my unpacker won't be able to find cdd file:
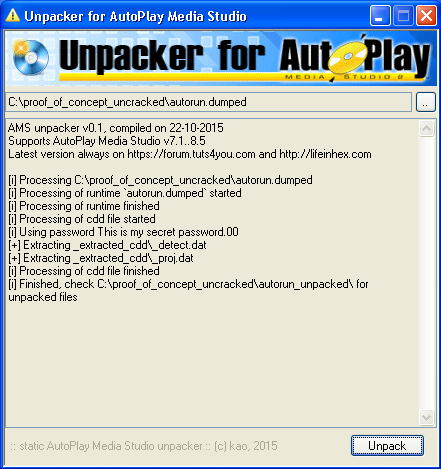
3) Process dump with unpacker:
- application.exe is packed and there is no cdd file.
This is the case of Reverzor. First you would need to unpack Enigma Virtual Box - for that you can use my other unpacker.. 😉 Now you have both exe and cdd files but exe file is still packed with ASPack. Again, you don't need to unpack ASPack properly, just run & dump process memory. Then process dumped exe with my unpacker.
- application.exe is hacked and the cdd file is renamed to something else;
This is a case of Idler. Author hacked AutoPlay engine and replaced file extension cdd with dll.
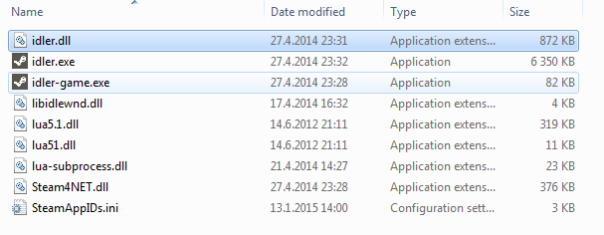
There is no way for my unpacker to cover all such scenarios automatically, sorry. Just rename idler.dll to idler.cdd and drop idler.exe on unpacker.
Conclusion
This was a small weekend project for me. If it also helps you in some adventures, I'm happy. If it doesn't help you at all, I don't care. 🙂
Download the unpacker from:
Note - due to technical reasons it's compiled against .NET 3.5, if you wish to run it on computer with only .NET 4.0 installed, create amsunpacker.exe.config with the following lines:
<?xml version="1.0"?>
<configuration>
<startup>
<supportedRuntime version="v4.0"/>
</startup>
</configuration>
And stay tuned for the upcoming post, where I'll explain how to write such unpacker from scratch!