About Error Messages
Users can't read.
Or maybe they don't want to read. I don't know.
But one thing I know for sure - you must make your tools foolproof. If your tool is showing an error message, make sure even your grandma could understand it. Otherwise you'll be getting lots and lots of invalid bug reports.
For example, this is the error message my EnigmaVB unpacker used to show (as reported by ho3ein at Tuts4You):
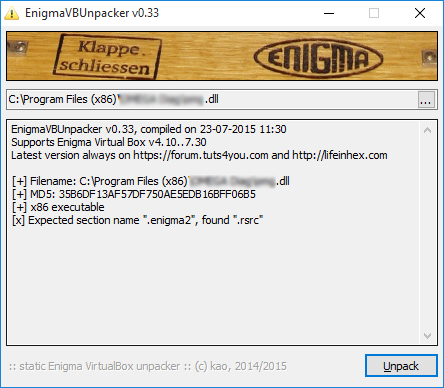
It seemed to be very clear to me. First, tool tells user all the versions of Enigma Virtual Box it supports. Then tool explains that it expects to see a PE section with a name ".enigma2" but it found section with a name ".rsrc" instead. To me it's absolutely clear what happened: this file is not protected with Enigma Virtual Box (or it's hacked).
But you won't believe how many times this gets reported as a bug.
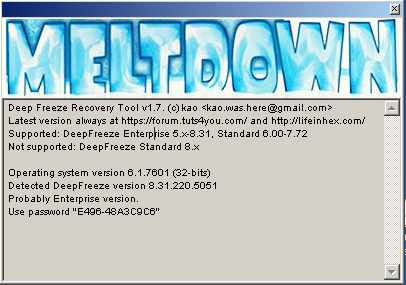
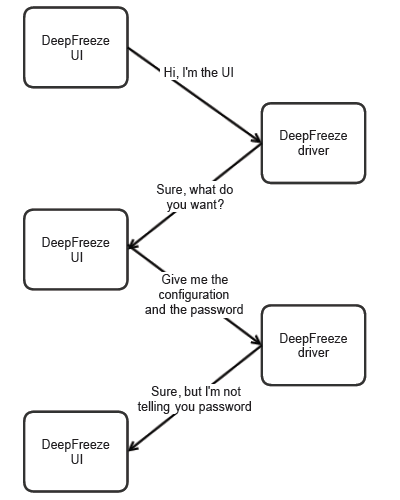
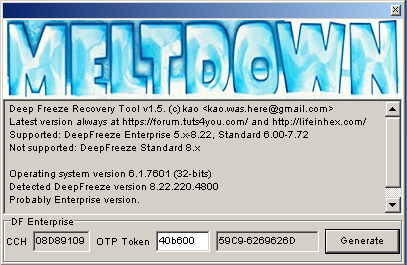
There was a similar problem with Meltdown. It clearly stated which versions of DeepFreeze it supports. Then it printed the detected DeepFreeze version. However, the error message didn't explicitly say "This version of DeepFreeze is not supported", it said "DeviceIoControl failed." It makes perfect sense from developer's point of view, but apparently is very confusing for users.
So, here are improved versions of my tools, fixing the error messages and some other stuff..
Improved EnigmaVB Unpacker
First of all, I fixed the error message. I also added detection and tested compatibility with the latest EnigmaVB v7.40. Hopefully, this will make users happier and less confused. 🙂
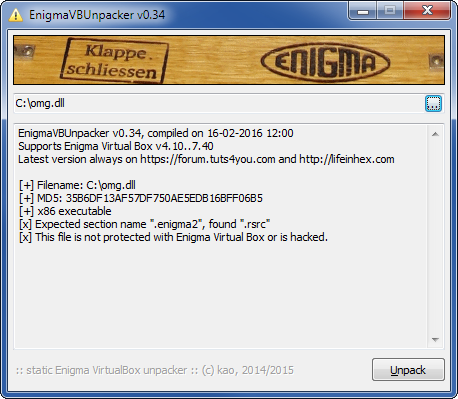
Improved Meltdown
Meltdown 1.7 fixes confusing error message with DeepFreeze Standard v8.x. Thanks to Alexander for reporting it.
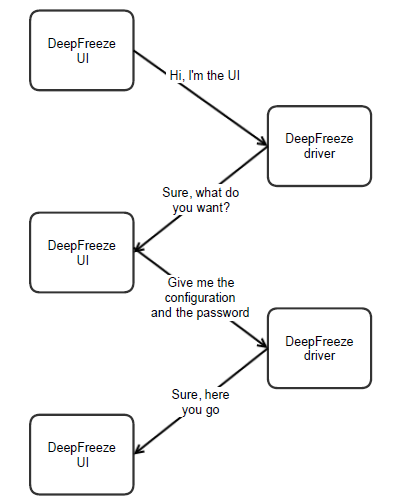
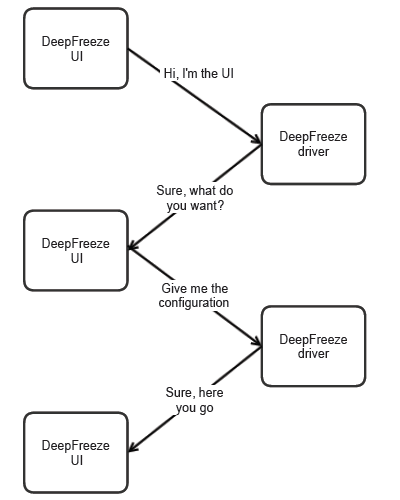
I also took a closer look at DeepFreeze Enterprise versions and found a way to make Meltdown more user friendly. If DeepFreeze Enterprise v7.20+ is detected, Meltdown will get OTP Token automatically and immediately generate correct password.
Download links
Enigma Virtual Box Unpacker: Please get latest version from this post
Meltdown v1.7: https://www.mediafire.com/?b0bamd3t2d6bbkq