There's not much for me to add. If you haven't read it already, do so - it's a great summary on modern day hacking.
Spanish original: http://pastebin.com/raw/GPSHF04A
English version by PhineasFisher himself: http://pastebin.com/raw/0SNSvyjJ
Breaking the world, one application at a time
There's not much for me to add. If you haven't read it already, do so - it's a great summary on modern day hacking.
Spanish original: http://pastebin.com/raw/GPSHF04A
English version by PhineasFisher himself: http://pastebin.com/raw/0SNSvyjJ
I've written about my troubles with Bitdefender AV solution before.. XXXX So, when my Bitdefender license expired, I was happy to switch to a different solution. I picked AVAST. In this post I'll try to summarize my my impressions after using it for one month.
Bitdefender 2016 insisted on me creating user account for their cloud management crapshoot before I was actually able to get installer and install the software.
On the contrary, Avast's setup was a snap. One, two, pick components, done.
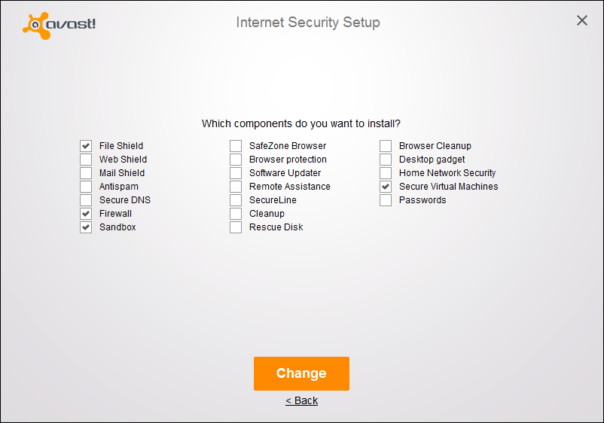
One minor issue I noticed - I'm quite sure Avast setup did not respect my choices and installed more components than I selected in the setup dialog. Or maybe I mis-clicked one checkbox. I'll give them a benefit of doubt.
Avast - 1 : Bitdefender - 0.
After all-dark-and-depressing Bitdefender UI, Avast feels much more brighter, colourful and cheerful. It feels much snappier and faster as well. Everything seems to be intuitive and easy to find.
Avast - 1 : Bitdefender - 0.
Avast has all its settings in one place. Bitdefender requires you to open each component separately to access its settings. Avast would be a clear winner here, but..
But good luck trying to find which apps are allowed or blocked by Avast firewall!
Firewall configuration is under "Settings", just like you would expect. From there you can configure "System rules" and "Packet rules". However, you won't find allowed/blocked applications there. Instead, you need to go to Tools->Firewall and locate teeny tiny "Application rules" hidden between "Firewall logs" and "Settings". WTF?
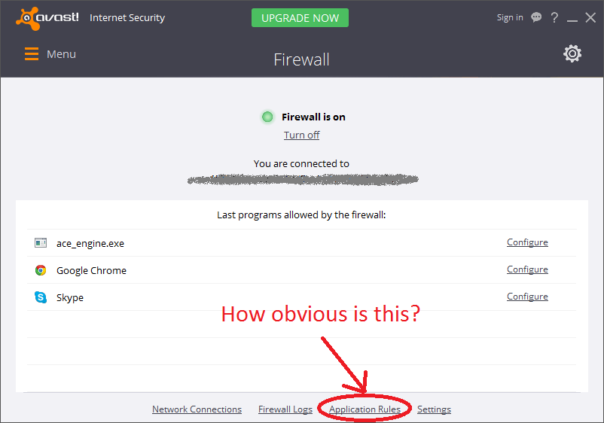
Taking that into account: Avast - 1/2 : Bitdefender - 1/2
Both antiviruses handle normal updates very well. No ads, no popups, no annoyances of any kind. Avast seems to have sort of ad hoc streaming updates 24/7 - or at least, that's what the Statistics tabs shows:
However... Today my Avast received a different kind of update that required restart. From what I can tell, this update replaced most of EXE/DLL files in the %PROGRAMFILES%\AVAST Software\Avast\ folder. After restart, my PC got stuck in semi-working state, services.exe and svchost.exe eating most of the CPU resources and Avast showing "try our new-and-cool-whatever-thing-I-don't-give-a-crap-about" advertisement. In addition to that, Avast claimed that it's firewall module cannot be started.
Few "repair installation" and Windows restarts later the problem disappeared. As a side effect - all my carefully set privacy settings were reset to defaults, "show offers for other Avast products" was enabled again and all File System Shield exceptions are gone.
Even though I really enjoy invisible 24/7 updates of Avast, I have to reduce Avast's score due to this major f*ckup.
Avast - 0 : Bitdefender - 1
As I described earlier, Bitdefender was far from being perfect. On the contrary, my first impressions of Avast were extremely positive. Great setup, aesthetically pleasing UI, plenty of user-configurable settings. Everything I could ask for!
However, first few weeks of using Avast has been nothing but a source of frustration.
Issue #1 - I've configured File System Shield to scan files only on execute. All scans on write or access are disabled for executable files using Avast's UI.
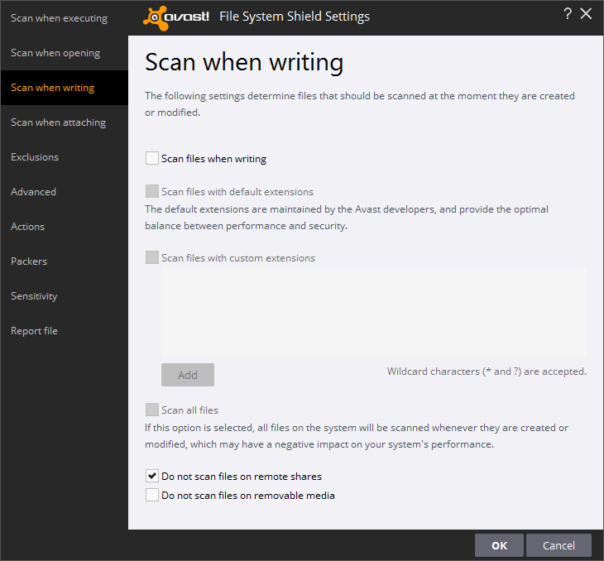
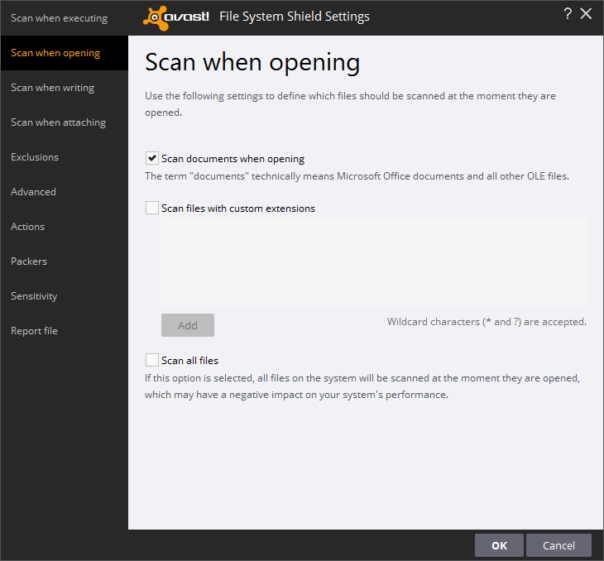
However, any time I copy-paste suspicious executable files from one PC to another using Remote Desktop Client, Avast File System shield pops up and blocks the copy operation. WTF?!
Issue #2 - There is no "Beggar off, I know what I'm doing" option in the detection dialog, even for heuristic detections. The previous issue wouldn't be a big one, if I had a possibility to dismiss detections dialog and continue copying files. But I can't.
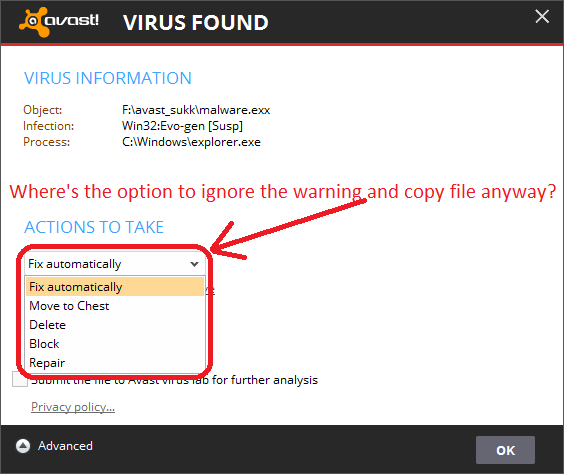
So, the only option for me is to disable File System Shield completely. That kinda defeats the purpose of having the antivirus, doesn't it?
Issue #3 - Myriad of "Win32:Malware-gen" and "Win32:Evo-gen [susp]" detections.
In effort to reduce number of false positives, I've set the heuristics and HIPS sensitivity to "Low". But even then Avast keeps producing plenty of detections on clean files like Goliath obfuscator, ScyllaHide and other reversing tools.
Issue #4 - Leaving statistics tab open for a long time will cause the CPU usage to go high. No idea what causes it, probably the braindead decision to use embedded Chromium and Flash to show the pretty graphs and stuff.
Taking all that into account: Avast - 1/2 : Bitdefender - 1/2
Avast is a great product - for your grandma's or neighbour's PC. But if you ever work with malware, cracked files or anything remotely suspicious, Avast's super-sensitive File System Shield will drive you mad.
I'll give it one more shot and try to tweak configuration files manually. But if I can't make it play nice, I'll be looking for a different solution for my PC.
Recently, several people sent me bug reports where my EnigmaVB unpacker failed to extract files. In all cases, the problem was caused by really large files, like 3.5GB in size. So, what's causing the problem?
EnigmaVB unpacker is a 32bit application written in Delphi. And Delphi streams are retarded. They look like they've been written in 1990s and were never updated. TMemoryStream uses a continuous memory range, so it can never support anything larger than 2GB. TFileStream internally uses longint, so it doesn't properly support files larger than 2GB. WTF?
So, I have two choices. I can either make a custom stream class in Delphi, or I can pick another framework and rewrite my tool to use that.
I'm not a programmer, I'm a reverser. I don't want to spend my time developing custom stream classes. I'd very much rather use this time breaking some code. So, say hello to .NET framework - my next version of EnigmaVB unpacker will be made in C#.. 🙂
While researching all the Delphi limitations and possible workarounds, I ran into this great article by Scott Hanselman. Reading both the post and the comments made me think a lot.
Does using Google to solve your programming tasks makes you less of a programmer? I don't think so.
In fact, I'm just lazy. Most people are. Why should I spend 30 minutes remembering basic algorithms for converting string to hex, if Google query can solve it in 10 seconds? Why reinvent the wheel and write CRC calculation from scratch? I'll just open StackOverflow and have a solution that's already tried and tested. It doesn't mean I can't do those boring tasks - I just don't want to.
How about you? Would you be able to write some tools without using Google and StackOverflow?
I was reading "How WIRED Is Going to Handle Ad Blocking" article and didn't know if I should laugh or cry. Here are some excerpts:
On an average day, more than 20 percent of the traffic to WIRED.com comes from a reader who is blocking our ads. We know that you come to our site primarily to read our content
Translation: we know that more than 20% of our users hate our irrelevant ads covering half the page. Fucking freeloaders, we can't make a penny out of them!
We know that there are many reasons for running an ad blocker, from simply wanting a faster, cleaner browsing experience to concerns about security and tracking software.
Translation: we know that ads can be obnoxious and sometimes distribute malware. Hell, big companies like Forbes distributed malware twice last year. We don't care, as long as we get paid.
So, in the coming weeks, we will restrict access to articles on WIRED.com if you are using an ad blocker. There will be two easy options to access that content.
Translation: WIRED just gave a middle finger to 20% of its users. What a great idea!
EDIT: lots of companies seem to be reacting to WIRED's move in one way or another. For comparison, here's the comment by Stack Overflow advertising managers. Now, that's an attitude that actually makes sense!
Last few days everyone is writing about passwords. How the most popular password last year was '123456', how it's all bad and that we all are idiots.
Let me tell you something - that's bullshit.
There are 2 types of resources: few important ones (my internet bank, company login, some RE forums, my blog, etc.) and the ones I don't really care about (2shared, codeproject and everyone else with mandatory registration).
For the important resources I have strong passwords. Unique ones with 8+ characters, mixed case letters, numbers and special symbols. You know the drill.
For everything else I'm using a throwaway email like Mailinator and password '123456'. Why? Because I don't give a crap. You want to crack my Codeproject login to download few files? Please do so. Hijack my Kickass Torrent account and post childish comment or two? Please. Use my account to download something from 2shared? Yeah, why not! I don't care! 🙂
So, next time someone runs around screaming about use of insecure passwords, ask yourself - where does this password list come from and who is this person making these statements? Maybe he just wants to sell you something?
Use a password manager such as {software_name} to organize and protect passwords, generate random passwords, and automatically log into websites
Right, let's make more FUD in effort to sell your software. Genius!
Stay cool, stay safe!
In part 1, I tried to explain reasons behind some of the decisions anti-malware companies make when designing their products. In this part I'll touch some other side-effects of those decisions and what they mean for power-users.
In general, I need a very basic antivirus protection - when I make a mistake during my reversing session or web browsing, it should stop malware from:
I'm not retarded and can read and think for myself - therefore I don't want "anti-phishing protection", "parental control", "safe banking", "vulnerability scan" or any other features aimed for persons who shouldn't be using Internet in the first place.
So, I always configure my antivirus to have just very basic on-access scan and firewall enabled, and all other components switched off. You can imagine my surprise when in last 2 days I have been greeted with these messages on 2 separate sites:
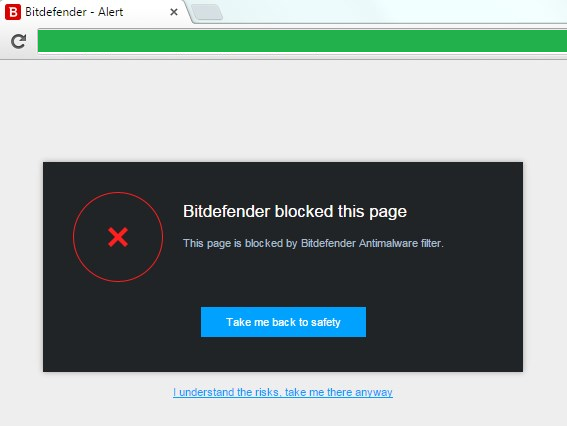
WTF guys, I have switched off every component I could - why are you still active?! And why are you bugging me with this nonsense?
I'm very sure that the answer is very simple: somebody in the UI/UX department decided that Bitdefender UI needs to be simplified. So, they took the UI that actually made sense, and fucked it up.
Here's how settings looked like in year 2013 (image (c) Softpedia):
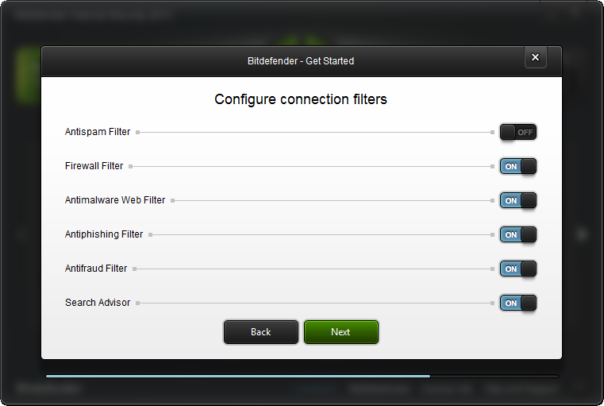
And here's how it looks in the Bitdefender 2016:
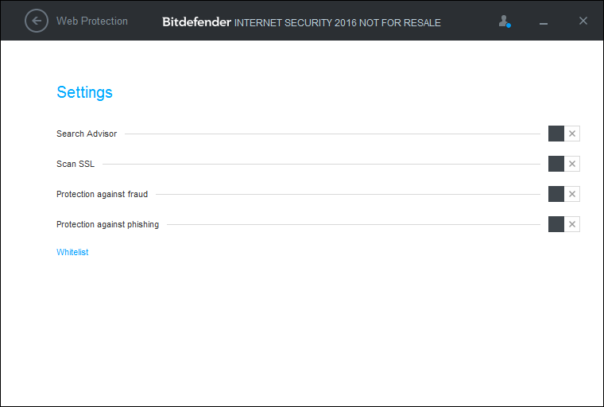
Antispam and Firewall have been moved to their corresponding module, but "Antimalware Filter" has disappeared altogether. After all, who would ever want to disable it, right?
To make matters worse, here's how the alert looked in Bitdefender 2015 (image (c) PCRisk):
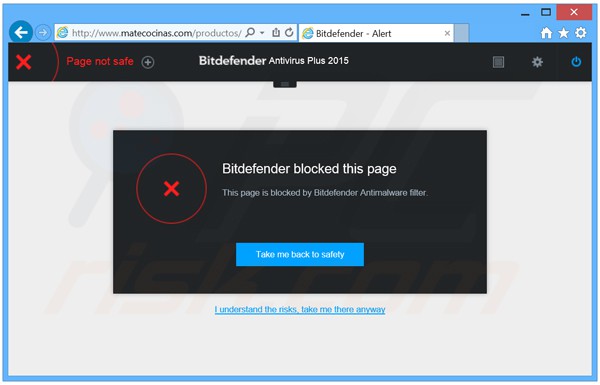
See, there was "Settings" button right at the top of alert page and you could disable "Antimalware filter" from there. Well, they "simplified" that option away as well. Geniuses!
Luckily, you still can. 🙂 All Bitdefender settings are stored in C:\Program Files\Bitdefender\Bitdefender 2016\settings\. However, to be able to modify files, you will need to start your computer in safe mode.
The file you're looking for is cloud.http.xml. Find your user name in it, and you'll see a section like this:
<user name="Administrator"> <active>true</active> <timeout>400</timeout> <status value="default">false</status> <status value="malware">true</status> <status value="phishing">true</status> <status value="fraud">true</status> <status value="untrusted">true</status> <status value="bank">true</status> <bank> <add> <domain value="" option="ask"></domain> </add> </bank> </user>
Apparently, there are more few settings which are hidden in the UI. I can only guess the exact meaning of them but - to be honest - I don't care. I just want this bugger to be gone from my machine. So, I changed "active" to "false" and for the good measure disabled each and every component as well. After a reboot, it all works the way I want, and I can access all the sites I want.
Great success! 🙂
What do you think - how large is "unlimited storage"? To me, word "unlimited" means, well, unlimited. "All you can eat". No restrictions.
For a year, Microsoft was offering unlimited storage with their Office 365 package:
Today, storage limits just became a thing of the past with Office 365. Moving forward, all Office 365 customers will get unlimited OneDrive storage at no additional cost. We’ve started rolling this out today to Office 365 Home, Personal, and University customers.
It was not a bad deal - for $6.99/month you could have both Office and unlimited storage.
Of course, some people decided to take Microsoft up on their offer and use that storage. After all, why not?
Fast forward one year. New post from Microsoft OneDrive team tells us this:
Since we started to roll out unlimited cloud storage to Office 365 consumer subscribers, a small number of users backed up numerous PCs and stored entire movie collections and DVR recordings. In some instances, this exceeded 75 TB per user or 14,000 times the average.
Good job guys! 🙂 If I had possibility to use unlimited storage, I'd use it as well!
But somehow Microsoft doesn't like it..
We’re no longer planning to offer unlimited storage to Office 365 Home, Personal, or University subscribers. Starting now, those subscriptions will include 1 TB of OneDrive storage.
...
Free OneDrive storage will decrease from 15 GB to 5 GB for all users, current and new.
So, now you know. "Unlimited" means "please, no more than 5 GB" in Microsoft-speak.
Today I was greeted with this great message from my old, trusted AdBlock plugin for Chrome:
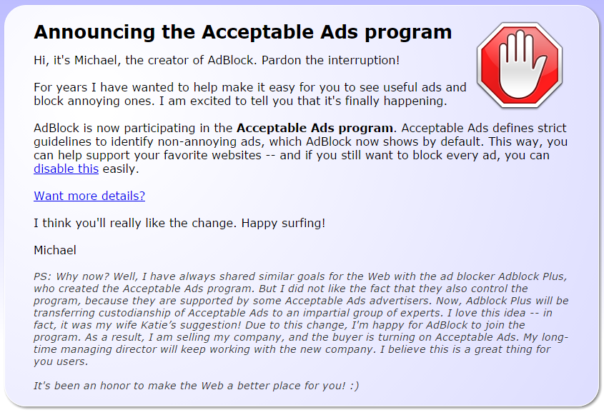
Hello?! There is no such thing as "Acceptable Ads". It's a misnomer, similar to "Enjoyable Rape".
Oh, well, good bye AdBlock, hello uBlock!
Everyone these days is talking about Volkswagen and how they made a software that cheated in vehicle emission tests. Volkswagen's stock price is tanking, CEO has been asked to resign, EU bureaucrats are looking into it and other major engine manufacturers are being investigated as well.
Let me give my opinion on all this affair.
Quote from EPA violation notice sums it up well enough:
The 'switch' sense whether the vehicle is being tested or not based on various inputs including the position of the steering wheel, vehicle speed, the duration of the engine's operation, and barometric pressure. These inputs precisely track the parameters of the federal test procedure used for emission testing for EPA certification purposes. During EPA emission testing, the vehicles' ECM ran software which produced compliant emission results
So, they added a piece of code to vehicles' ECU block that was able to detect testing mode and then adjust engines' operating parameters. It's very similar to what ECU tuning shops do, except Volkswagen did it to reduce emissions in certain cases and petrolheads do it to achieve best possible performance from their cars.
Some dude on hackaday sees a big ethical issue here:
An engineer, either in Volkswagen or less likely at a subcontractor, signed off on code that would defeat the entire purpose of EPA and Clean Air Act regulations. Someone with the authority to say ‘no’ didn’t, and this code was installed in the electronic control unit of millions of cars.
Say what?
This dude apparently knows nothing about how corporations work. There is no way in hell that some engineer came to his boss and said: "Hey, I just figured out a way to cheat in USA emission tests, do you think it will be useful for our company?".
No. Fucking. Way.
I'm convinced that this decision came from the middle management and was passed down to engineers. Something like: "We don't care how you do it, just make sure our diesel engine passes those tests. Just don't tell us how you managed that." Plausible deniability, you know.
However, dude from hackaday is absolutely right in another aspect - some engineer will likely lose his job over this. It's not because he did something wrong, it's because the company needs a scapegoat. Just like they sacrificed Chief Executive Martin Winterkorn - CEO had nothing to do with a scandal, it's just one of those steps company needs to do to make a good PR.
As strange as it sounds, they got caught by accident. International Council on Clean Transportation (ICCT) wanted to convince European bureaucrats to implement strict US standards for diesel emissions in EU. So, they hired West Virginia University’s Center for Alternative Fuels, Engines and Emissions (CAFEE) to run tests in the field. And as interim director of CAFEE explains:
They rented VW diesels, measured their tailpipe emissions on the road and compared them to measurements on the same cars made in the lab. The discrepancies were huge.
So, the scientists made some presentations in 2014, published their research online, and nobody except USA bureaucrats cared about it. Until last week, that is.
Now suddenly everybody is acting as if the world is going to be destroyed by this.
Let me answer this question with a quote from the original EPA news release:
These violations do not present a safety hazard and the cars remain legal to drive and resell. Owners of cars of these models and years do not need to take any action at this time.
I'll give you a moment to think about that.
482'000 cars in USA alone. 11'000'000 cars in the whole world. 5 years. Exceeding NOx limits 20 times. Affected cars are not a safety hazard. USA cities are not covered in black smog. In fact, nobody noticed anything for 5 years. What does it tell you?
To me, the answer is simple - those NOx limits are fucking bullshit. They make your car more expensive and reduce horsepower of your engine. They don't save the planet. They are there because some bureaucrat needs to justify his puny existance in some environmental agency.
Don't get me wrong - I do care about the environment. But you are not helping the environment much by limiting already small emissions of NOx. Instead, you should rather look at the Asia and their industrial practices. For example, burning down forests in Sumatra - which produce so much smoke that the entire Singapore city (being 80 kilometers away from Sumatra!) has its air quality deteriorating to a "very unhealthy" range. Or look at the half of China's rivers which are polluted with industrial waste and fertilizers. Now, that is something that actually needs fixing!
Volkswagen knew these regulations are bullshit and won't save the Earth. They knew their engines can't pass them. So, they had balls big enough to give all bureaucrats the finger and cheated their way through.
I say - good for them! In my scorebook it's "Volkswagen 1, Bureaucrats 0".
Mandatory disclaimer - all views in this article are my own and in no way represent views of my employer or my coworkers.
Last few weeks I noticed several gposts about antiviruses, False Positives and how bad the situation is. For example, this essay from atom0s and this complaint (reg required) by mudlord. And then there is this epic rage by evlncrn8. 🙂
To understand why antiviruses work this way, you need to consider plenty of factors. So, let's take a quick look.
It usually starts with a group of skilled guys wanting to save the world. They make a great product, people like it, company makes some money, more people like the product, company grows even more and so on..
But as company grows, priorities change. The bigger and more popular the company gets, the more managers and investors it attracts. Those guys usually have no clue about technology behind antivirus. And they don't care about technology, they only see numbers and dollar signs everywhere.
And then the primary goal of company changes to making profit for shareholders.
Let's face it - readers of my blog are not the usual antivirus users. Antiviruses are used by everyone - from extremely skilled IT geeks to Granma Millie living in the retirement home. And this causes second biggest problem - big companies cannot make product just for skilled IT geeks, as nobody else will be able to use it. You can't make a product for the average user either. You need to make something that even Granma Millie can use.
And that's why most software products in recent years get dumbed-down - managers think that they need to do "inclusive designs" - so even the most retarded of users can use the product.
One of the most common complaint I hear is that all antivirus products are becoming a huge bloatware. There are several reasons for that. First, product managers just don't know any better.They look at all competitors - if Company A has feature X, you need to have feature X, no matter if it actually makes sense or not. Second reason is that company somehow needs to sell new version of product. You can't say - this version is the same as the old one, we just changed colours and moved buttons around. No, you need to have something like "New version, now with features Z and Q!"
It's not the best way but it's certainly the easiest!
When you are purchasing a new car, you probably search for the reviews online. You probably do the same when you decide to move to new city, plan your vacation or make any other big decision. That's just normal.
And it's the same with antiviruses - most people will either get a recommendation from someone they trust, or they'll search for reviews online. So, the companies need to invest a lot in PR and make sure their product looks good in tests and reviews.
Testing methodologies most of the times are not representative of any real-life experience of ordinary users. Testers take whatever pieces of malware they can find and test AV products against them. They don't distinguish between different types of malware, sample prevalence or geographical distribution.
I'm sure you feel much safer knowing that your antivirus protects you against a worm that is distributed only through Chinese QQ messenger, or that very nasty banker attacking only Brazilian banks. Don't you?
To test False Positive rate, testers check number of files from popular download sites like CNET, Softpedia or PCWorld, or collected from European SMB companies. Of course, AV companies do the same thing and try to make sure they have no false positives on those sites. But if you're a small software dev and distribute your software using other means, or don't target SMB companies - well, bad luck. False Positive on your file doesn't influence test results. 🙂
It's a load of crap - but every company is still doing it because lots of potential users rely on such "tests" before buying antivirus. Some companies even cheat in tests.
Number of new malware and other crap these days is increasing exponentially. According to McAfee Quarterly Threat reports, ~4 million new malware samples appeared in the Q1 2009, ~7mil in the Q1 2012, ~32mil in Q1 2014 and ~48mil in Q1 2015.
Think about it. How can you process 48'000'000 samples?
The answer is simple - automation, automation and more automation. Malware classification is hugely automated process. Does the file look weird? Does it do weird things? Was it sent out in a spammy email? Is it encrypted to prevent automated analysis? Was it protected using stolen Themida? Do other antiviruses think it's bad? Game over, classified as bad!
Sure, sometimes some legitimate software gets classified as bad. In this scale, it's bound to happen.
If automation is not able to classify file, malware researchers will need to analyze it manually. This is where big data software, statistical models and cluster analysis come in. They alert researchers to traffic anomalies, suspiciously similar thousands of files and other "interesting" stuff. Files get prioritized based on prevalence, number of users affected and other factors. And, of course, the bigger the issue, the faster it gets attention from a real human being.
So, if your legitimate software is classified as bad and it affects all your 50 users - it's not because AV company hates you or your product. Really, they don't hate you. They just don't know you even exist. So, the sooner you let the AV company know about the problem, the sooner they will fix the issue.
But hiding your head in sand and saying "I don't have to time to play a cat and mouse game with anti-virus companies" will get you nowhere.
Think about the points I just made. Your product needs to bring company money. You need to make a product Granma Millie can use. Your product needs to behave well in tests. Given the requirements, no matter how skilled the developers and researchers are, the end product will be...
Well, it will be just like the product you're getting now - dumbed-down, feature-bloated money-making piece of software that fares reasonably well in artificial tests.
You're living in the era of globalization and money-making corporations. Deal with it.